Cloud Enterprise Architecture, Cloud Networking
Case Study: Designing An AWS Enterprise Cloud Network Architecture
Background
A large government agency was using two geographically separated on-premise data centers and needed to implement a target Cloud Hosting Environment (CHE) to migrate all their mission critical applications. The agency did not have any AWS accounts or an existing footprint in the Cloud.
Analysis
STS conducted an agency application and infrastructure assessment on the virtualized VMware environments, Load balancers, and the Network Operations Center (NOC) managed Classless inter-domain routing (CIDR) Internet protocol (IP) ranges at the two data centers.
Solution
AWS initially launched GovCloud for secure usage of the AWS environment for Federal agencies. There was only one region available as us-gov-west-1 without the availability of a mirroring site needed for robust disaster recovery. About eighteen months later, a second region for GovCloud opened as us-gov-east-1 and the networking architecture was implemented in two phases.
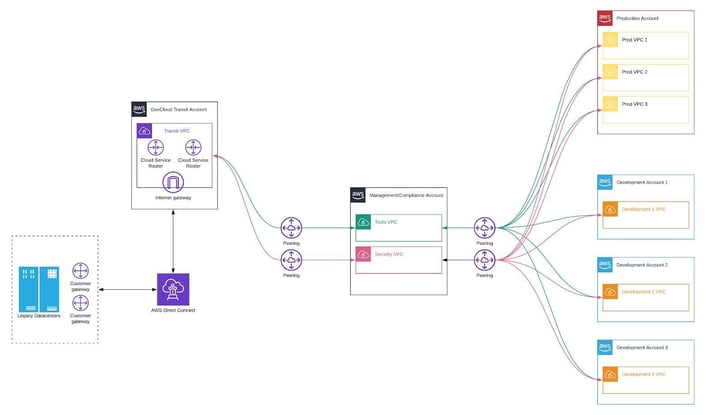
The customer’s defined Internet Protocol (IP) range was allocated across both GovCloud regions. To ensure separation of concerns and environments, STS engineers implemented a hub and spoke model. A central management Virtual Private Cloud (VPC) Network was connected to both non-production and production networks via a combination of peering and virtual network appliances. Cloud Service Routers (CSRs) were used to establish secure connectivity to other DHS components and third party stakeholders.
The Solution Architecture diagram shows the separation of concerns using VPCs, and internal and external connectivity, via network peering connections and CSRs.
Benefit
STS created a clearly defined division of network traffic and a designated area for shared tools by separating AWS accounts by environment and utilizing a hub and spoke approach.
The customer was able to easily manage access control, restricting access to production systems, while allowing increased speedup in development. To keep the AWS account footprint small, fewer CSR’s and vSRX’s (virtual security appliances) were needed to ensure connectivity back to external resources. The STS solution enabled stable networking and account separation, resulting in fewer network outages and a reduced security risk posture.
Production Account Diagram
STS Engineers determined that a programmatic approach to the project would provide the most streamlined access to GCP resources and services.
Like what you're reading? Start a conversation by booking a meeting with us today.
Download the Proven Strategies for Agency Legacy Application Migration Ebook to learn migration considerations, proven best practices, and government success stories.



%20SERVERLESS%20PROJECT.png)