AWS, cloudsecurity, Case Study, Security
Case Study: Enterprise Security Hub Implementation
 Background
Background
The customer, a law enforcement and public safety agency, did not have proper cloud security policies, standards, and best practices in place within their cloud environment. The customer was heavily focused on compliance with Center for Internet Security (CIS) security policy, but did not implement or enforce cloud security best practices and standards while they were transitioning to the cloud.
They had the following issues:
- Security rules/standards were often broken by users and administrators,
- Public access to accounts and S3 buckets,
- Inactive accounts were not deactivated,
- No multi-factor passwords,
- Passwords were not periodically changed/reset.
Security was not continuously monitored and remediation was manually intensive work.
Analysis
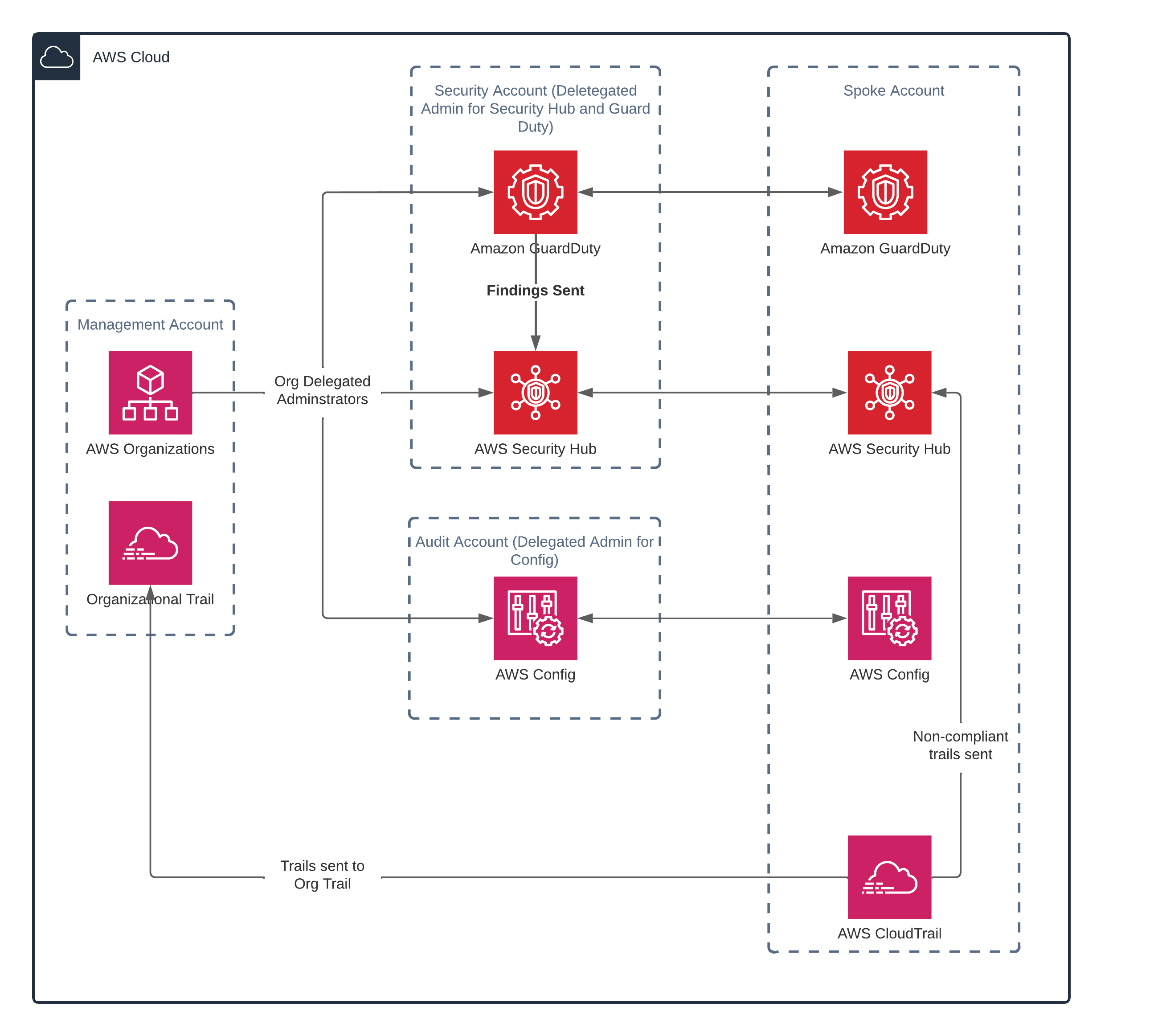
STS proposed implementing AWS Security Hub to provide a centralized and comprehensive view of the health of the environment. Leveraging the Security Hub with other AWS tools facilitates automated detection, remediation, and reporting of security issues.
Solution
We implemented AWS Security Hub with additional AWS managed services:
- AWS CloudTrail - (along with AWS Config & AWS GuardDuty) provides AWS resource configuration inputs to Security Hub.
- AWS SNS Topic - used for providing consistent notifications to the Cloud Hosting Environment tenants. Each of the Lambda functions publish remediation actions to the standard SNS topics.
- AWS Organizations - provides centralized policy-based account management. enables the implementation of CloudTrail and log trails and helps with provisioning tenant accounts by automatically setting policies for those specific accounts.
- AWS Identity Access Management (IAM)- automatically assigns administrative roles to tenant accounts
Benefit
STS leveraged the aforementioned AWS services to implement and enforce agency security policies, automatically detect and remediate security vulnerabilities or issues, and establish enterprise cloud security standards/best practices using cloud automation. With a centralized and comprehensive dashboard of the entire system, our client can continuously monitor and address issues with greater efficiency. In less than 10 weeks, the percentage of non-compliant AWS Foundational Security Best checks went from 20.32% down to 18.25%, and CIS noncompliance went from 32.99% 30.84%.
AWS Security Hub was used to identify and group similar findings (i.e., networking, logging). These finding groups were then examined on a case-by-case basis to determine the best way to remediate them, including through automated scripts, manual configurations, or reports sent to designated personnel. Most of these problems involved a two-stage process where STS created Lambda functions to report on the problems for later manual remediation.
The security team has access to every tenant account and can conduct audits at any given time. Leveraging AWS SNS Topic, rules are configured to provide reporting for each account. Security reports are transparent and key security stakeholders are immediately notified when issues arise. Each tenant account has a configured rule in place which automatically notifies system administrators when an IAM user has been inactive for 90 days. These AWS tools enable the security team to continuously monitor accounts in an integrated and centralized manner, making audits and troubleshooting much more efficient. Once almost the customer reached near 100% compliance with these issues, the Lambda solutions were switched to automated governance functions that would maintain the desired configuration(s) for all of the affected resources.
The implementation of these tools enables the team to proactively remediate security issues rather than taking a reactive approach to address them.

%20SERVERLESS%20PROJECT.png)