Cloud Enterprise Architecture, DevSecOps, Cloud Governance & Compliance, Serverless, Case Study
Case Study: Improving Cloud Operations With Proactive Resource Management
Background
A large U.S. Government Agency had to migrate over 80 applications from their data center into Amazon Web Services (AWS) and Microsoft Azure (Azure) Cloud Hosting Environments (CHE). The customer had a very tight deadline to migrate all of its applications before the hosting service shut down its legacy data center. There were a number of expectations for this migration effort: a) development teams should be empowered to provision and manage their own cloud infrastructure, b) teams should use and embrace modern automation and DevOps practices, c) teams should utilize open source tools, and d) infrastructure should be managed in a way that was transparent to the Office of the CIO thus eliminating shadow IT office requirements.
Analysis
Simple Technology Solutions (STS) identified a number of traditional infrastructure engineering tasks that could be managed by development teams via automation. Using tools such as Chef, Terraform, and Jenkins, STS engineers provided these solutions to application teams. However, many application teams continued relied on legacy infrastructure engineering staff to complete these tasks in lieu of automation. After discussing legacy dependency and barriers to cloud migration with government IT project managers and team leads, STS identified a large skill and cloud technology knowledge gap for many team members.
Solution
To address the identified cloud technology skills gap, STS team designed a template for a series of three ‘onboarding’ meetings. These meetings were designed to provide a personalized, user centric introduction to the cloud hosting environment. The training was customized to the cloud service provider and the application’s specific technology stack.
First meeting: Focused on ensuring all team members had access to all necessary cloud automation and devops tools such as a) AWS/Azure console access, along with the associated Software Development Kit (SDK), b) Terraform installed in the development environment, c) Chef Server access, and Chef’s SDK, d) Enterprise Github access, and e) access to the Jenkins CI/CD server. By assembling the engineering teams and government approvers in the same location, approval issues and troubleshooting times were reduced from weeks of emails to a single morning meeting.
Second meeting: Provided initial code for Terraform and Chef so the team could create their own infrastructure to be automatically hardened, secure, and compliant with agency requirements. At the end of this meeting, the team had a repository in Github Enterprise so they could continue developing Infrastructure as Code (IaC).
Third and final meeting: Discussed cloud native application design with the Cloud Architect. They identified a goal to develop Jenkins pipelines for automated deployments and explored opportunities to use cloud technology to reduce operational requirements and focus on development.
Benefit
As a ‘develop once, deploy many times’ solution, the networking IaC solution delivered exponential business and technical value after the initial development period. With the new solution, the agency was able to build out highly available applications with robust disaster recovery solutions to reduce the likelihood of outages. Providing the solution as IaC allowed for rapid development, testing, and review, leading to faster implementation and updates. Finally, since the IaC code deployed the same solution in an identical manner each time, human error was eliminated and there were no issues reported in the rollout of the new cloud environment applications.
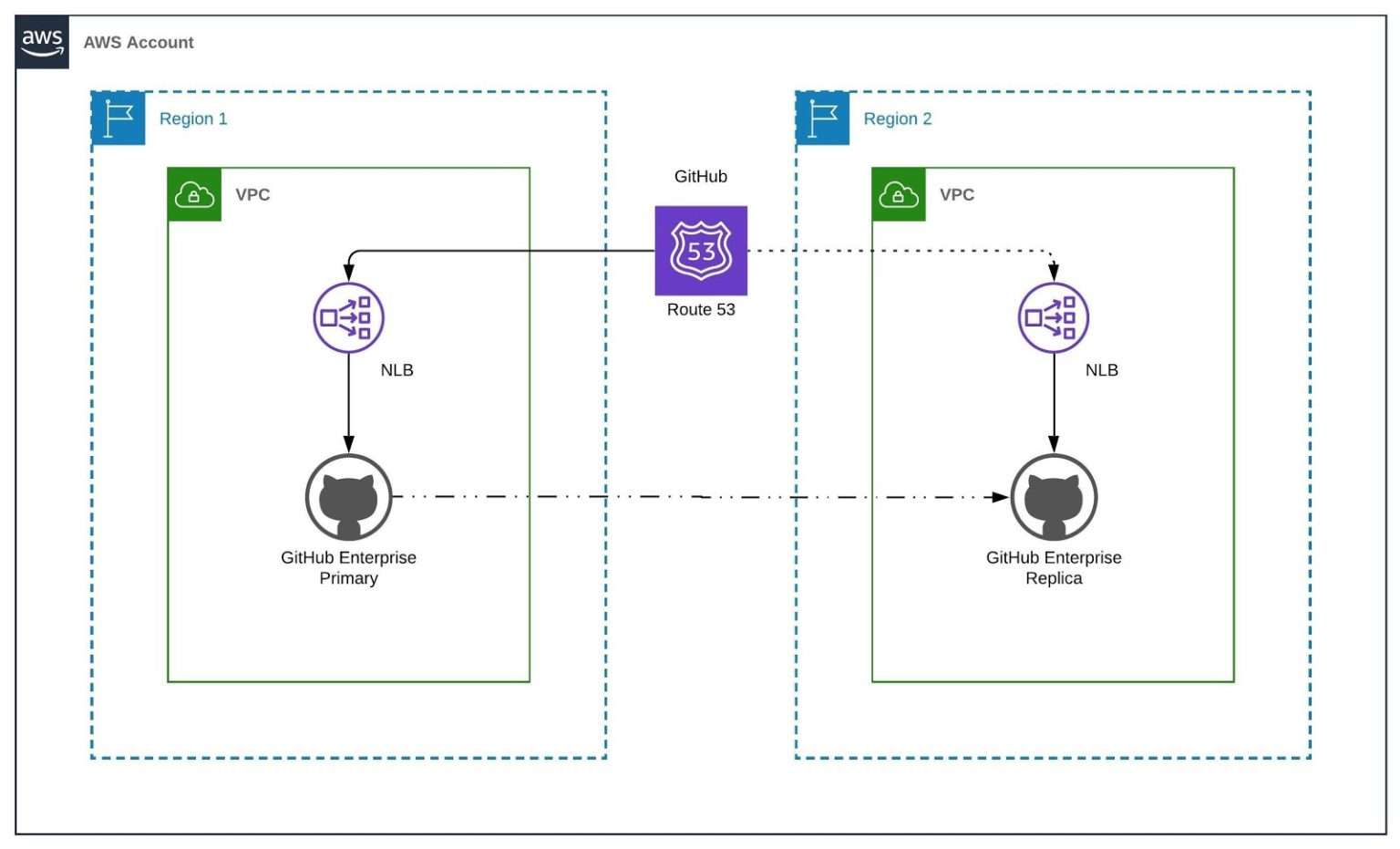
STS leveraged AWS native services and creative thinking to overcome the common challenge of account provisioning and overage when migrating to the cloud.
Like what you're reading? Start a conversation by booking a meeting with us today.
Download our Ebook - Guide to Achieving Cloud Security for Federal Agencies to learn how you can ensure your federal agency is prepared with solid cloud security.